
If you or your company stores, processes, and transmits sensitive cardholder data, it’s vital you follow compliance requirements set by the PCI DSS (Payment Card Industry Data Security Standard). PCI DSS sets 12 key requirements for businesses covering everything from firewalls and encryption to logging, testing, and clear security policies.
The cost of non-compliance can be huge, with risks including fines, loss of payment processing, data breaches, lawsuits, and reputational damage. Ultimately, PCI compliance helps prevent fraud, protect sensitive information, and build trust with customers and processors.
According to the Verizon Payment Security Report, Only 14.3% of global organizations maintained full compliance with PCI DSS at interim validation, representing a clear downward trend in full PCI DSS compliance since its 2016 peak. Industry research consistently demonstrates that organizations maintaining full PCI DSS compliance experience significantly fewer data breaches and lower incident costs than non-compliant organizations. Comprehensive compliance doesn't just check boxes—it creates genuine security resilience that protects both cardholder data and business continuity.
This article will help you understand the core PCI DSS requirements, explain how each one protects cardholder data, and outline practical steps your business can take to achieve and maintain full compliance with confidence.
Read on to learn more about these all-important requirements and how you can ensure you meet them.
What Is PCI Compliance?
PCI compliance refers to the data protection standards set by the Payment Card Industry Data Security Standard (PCI DSS), which require organizations that process, store, or transmit cardholder data to implement strong technical and physical safeguards. Compliance involves more than just encryption—it includes maintaining secure firewall and network configurations, enforcing strict access control and authentication protocols, regularly testing and monitoring systems for vulnerabilities, and documenting clear information security policies that guide employee behavior and vendor management.
Ultimately, being PCI compliant means continuously assessing and improving your security posture to protect the cardholder data environment (CDE), minimize risks of breaches, and preserve the privacy and financial trust of your customers. Whether you’re an online merchant, retailer, or service provider, ongoing compliance helps ensure that your defenses evolve with emerging threats and that your business remains resilient and credible in today’s data-driven economy.
The 12 PCI DSS Compliance Requirements
The 12 PCI DSS compliance requirements fall under six specific control objectives. You should build and maintain a secure network and systems, protect account data, maintain a vulnerability management program, implement strong access control measures, regularly monitor and test networks, and maintain an information security policy.
These categories, and the 12 requirements, are designed to protect cardholder data regardless of where or how it’s stored, processed, or transmitted. The requirements apply to businesses of all sizes.
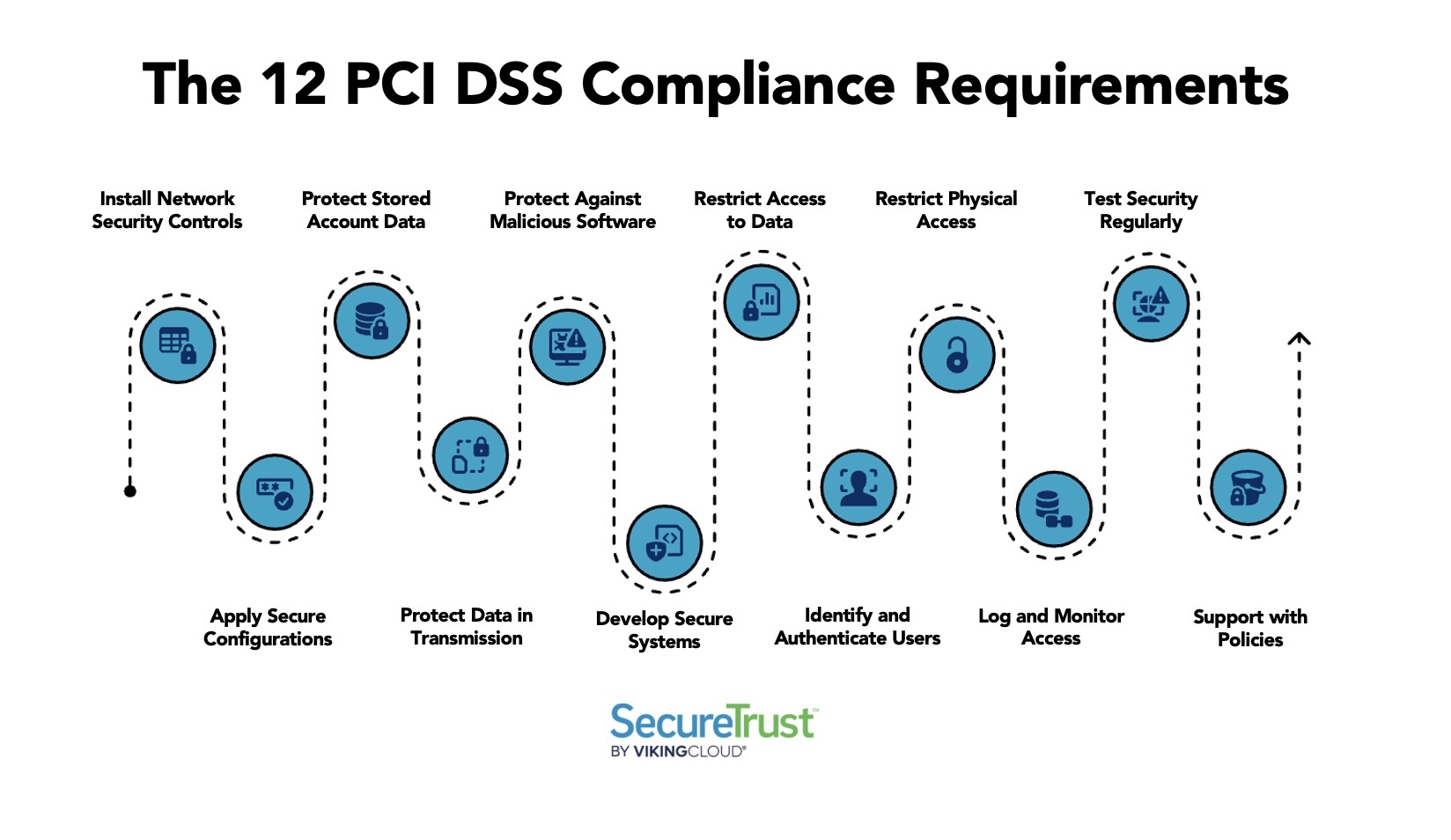
Here’s how each of the individual requirements break down:
1. Install and Maintain Network Security Controls
You should always install and run a functional firewall and test the strength of your connections to prevent vulnerabilities. Doing so helps to restrict external threats and to prevent hackers from accessing your infrastructure.
2. Apply Secure Configurations to All System Components
Always check and adjust user access controls, change passwords regularly, and re-secure configurations and functionality throughout the year. This includes removing unnecessary services/protocols or disabling default accounts and ensuring all password settings shared between internal, networked devices, and portals are audited.
3. Protect Stored Account Data
All data you store should be secured and encrypted (cardholder information included) to prevent interception. You should also assess any vendors’ security policies, reduce your attack surface by limiting storage, and physically locking and protecting data on-site.
4. Protect Cardholder Data with Strong Cryptography During Transmission Over Open, Public Networks
You should apply encryption standards of at least TLS 1.2 or higher to any public applications and live websites. It’s also important to truncate and encrypt any cardholder information you store so it is incomplete and unreadable. Above all, avoid sharing card data in its entirety through all channels, particularly instant messengers and email, where it may be intercepted.
5. Protect All Systems and Networks from Malicious Software
Deploy and maintain up-to-date anti-malware and antivirus solutions on all systems commonly affected by malware ensuring automatic updates and regular scans are enabled. Organizations should configure anti-malware to perform periodic scans, generate audit logs for all detection events, and prevent users from disabling or altering protective mechanisms. Systems must be actively monitored to ensure anti-malware remains current and operational, with alerts triggered for any lapses in protection or failed updates.
6. Develop and Maintain Secure Systems and Software
Ensure your policies and processes keep software and systems up-to-date with the latest security patches and firmware requirements, and that good security practices are maintained. Always develop applications for mobile and web use in secure environments, with optimal protective measures.
7. Restrict Access to System Components and Cardholder Data by Businesses Need to Know
Only allow access to cardholder data to authorized parties/personnel, and those who require the information for legitimate purposes—known as the last privilege model. In addition to restricting digital and physical access based on business need-to-know, organizations should regularly review access rights, monitor entry logs, and track visitors to maintain accountability within the cardholder data environment (CDE).
8. Identify Users and Authenticate Access to System Components
Assign unique user IDs to all personnel, ensuring accountability and traceability. Users must authenticate using strong credentials before accessing systems that could impact the security of cardholder data. Avoid basic password protection—always secure sensitive systems and cardholder data with additional measures such as biometrics, multi-factor authentication (MFA), smart cards, and tokens. Also enforce password complexity requirements, regular password changes, and lockout policies after failed login attempts.
9. Restrict Physical Access to Cardholder Data
Install and maintain physical security equipment to monitor data storage on-site. Use secure physical storage and MFA to lock down data offline. Retail operations also benefit from physically locking and monitoring Point of Interface (POI) terminal equipment to prevent internal tampering.
10. Log and Monitor All Access to System Components and Cardholder Data
Maintaining detailed access logs, audit trails, and real-time monitoring of all activity within the cardholder data environment (CDE) is essential for detecting and preventing unauthorized access. Using tools like Security Information and Event Management (SIEM) and File Integrity Monitoring (FIM) enables continuous log review, helping organizations quickly identify suspicious activity.
11. Test the Security of Systems and Networks Regularly
Regular testing and security assessments are essential to verify that controls remain effective and compliant with PCI DSS standards. Conduct quarterly external vulnerability scans using an Approved Scanning Vendor (ASV) and internal vulnerability scans at least quarterly to identify and address security weaknesses. Perform external and internal penetration testing at least annually and after any significant change to verify that security controls remain effective. Also test wireless access points quarterly if applicable, deploy intrusion detection/prevention systems (IDS/IPS) to monitor network traffic, and implement file integrity monitoring (FIM) to detect unauthorized changes to critical files. All testing must be documented, with remediation tracked and verified through follow-up scans.
12. Support Information Security with Organizational Policies and Programs
Ensure that security policies are available for employees to follow, and that chains of command and accountability are clear and easy to understand. Regularly refresh all policies and top-up training to combat threat evolution, building towards a flexible and proactive incident support plan.
What Does it Cost to be PCI Compliant?
The costs of becoming PCI compliant (and staying that way) vary depending on the size of your company and how many transactions you process annually. Many businesses face costs of five to six figures purely to keep compliant, though the costs of non-compliance can be much higher long-term.
PCI DSS determines your basic assessment and reporting requirements based on four key levels for vendors, and two for service providers. The more transactions you process per year, the more you can expect to pay in basic scanning, auditing, and reporting. However, precise PCI compliance costs can also escalate further depending on the time and effort needed to bring your company up to code.
What Happens If You’re Not PCI Compliant?
Failure to comply with PCI DSS can lead to card processor fines, loss of service privileges, customer lawsuits, data compliance penalties, insurance claims filed against you, loss of business, and client cancellations.
The cost of non-compliance is considerably higher, long-term, than what you pay to establish and maintain it. According to IBM, data breaches cost businesses an average of $4.4 million every year.
Non-compliance not only puts you at risk of financial and business curtailment via your processors, but also leaves you wide open to loss of reputation and revenue. Data breaches can kill consumer trust, meaning you’re facing fines, legal action, and a severe loss of business if you don’t comply.
Following PCI DSS requirements carefully ensures you keep your business practices compliant, your customers’ data safe, and your reputation robust in an ever-changing threat landscape. For more information on how to achieve and maintain PCI compliance, contact our team for solutions tailored to small businesses and enterprises alike.
PCI Compliance Requirements FAQs
What is a Self-Assessment Questionnaire (SAQ) and which one applies to my business?
A Self-Assessment Questionnaire (SAQ) is a validation tool that helps merchants and service providers evaluate their PCI DSS compliance. There are multiple SAQ types—such as A, B, B-IP C, C-VT, and D—each designed for different payment environments based on how and where cardholder data is handled.
What happens to PA-DSS-validated payment applications now that PA-DSS is retired?
Payment applications that were previously validated under PA-DSS must now transition to the PCI Secure Software Standard to remain current. While older PA-DSS applications can still be used in existing deployments, new validations must meet the updated Secure Software framework.
Does the PCI Security Standards Council enforce compliance directly?
No. The PCI Security Standards Council (PCI SSC) develops and maintains the standards, but enforcement is handled by payment brands, acquirers, and processors. These entities determine penalties, validation requirements, and deadlines for non-compliant organizations.
How frequently must I perform scans, tests, and audits to stay compliant?
PCI DSS compliance is an ongoing process. Businesses must conduct quarterly vulnerability scans using Approved Scanning Vendors (ASVs), perform internal and external penetration testing at least annually, and maintain continuous monitoring and logging to detect and prevent potential threats.
How does PCI DSS address access control and physical security?
Access to the cardholder data environment (CDE) must be limited to personnel with a business need-to-know. Use Active Directory (AD), Lightweight Directory Access Protocol (LDAP), or other identity and access management protocols to enforce role-based access control (RBAC), and secure data with locked servers, locked cabinets, video surveillance, and multi-factor authentication (MFA).
What should an information security policy include?
A strong information security policy defines how data is handled, accessed, and protected. It should include employee training, background checks, incident management, and clear documentation of security procedures. Regular reviews of third-party vendors and alignment with cybersecurity frameworks help ensure risk minimization and compliance.
How can organizations strengthen password and authentication controls?
Follow NIST password guidelines by avoiding vendor-supplied defaults, assigning unique IDs, and requiring strong passwords with two-factor or multi-factor authentication applications. Continuous audit logs and audit trails help detect and prevent identity theft or unauthorized access.
Senior Product Marketing Manager
SecureTrust
More Blogs

.avif)
.jpg)




