CCPAThe California Consumer Privacy Act is Evolving

Thanks to those who attended our webinar on CCPA! If you missed the webinar, click here to view or keep reading for a recap!
CCPA is the acronym used to describe the California Consumer Privacy Act. To read the full text of the law, and see the latest updates, the best resource is the California Attorney General’s Office website. The CCPA establishes a new regulatory scheme in the state of California that adds new requirements for any company that collects, sells, or buys Personal Information (PI) about people who reside in California.
Those new requirements include the following:
- Privacy Policy & Disclosure
- Access to and portability of PI
- PI destruction / deletion
- Opt-out program
- Non-discrimination
CCPA spends a lot of time defining what PI is, and recent updates also help understand what does not fit in the law’s definition of personal information. The law is very verbose, but in summary, describes sensitive information about individual people that can be directly linked to that individual. The California Attorney General’s office published an update to the law on Feb 10, 2020, that adds clarification about when items defined as PI in the law are not PI without a link directly to a consumer.
The first step in assessing CCPA compliance is to determine if you are subject to CCPA.
I have created this helpful diagram to determine if CCPA applies to your business:
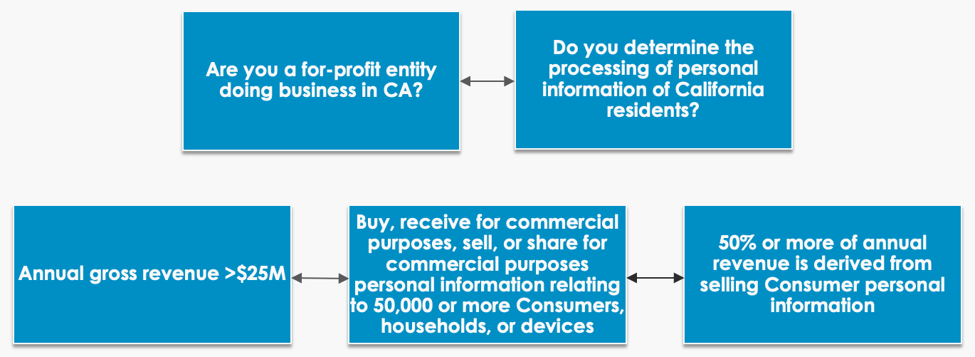
If you meet either requirement in the first row and any of the three in the second row, then CCPA will apply to you.
In our recent webinar, I outlined six steps to CCPA compliance:
- Determine your entity types – CCPA defines three different entity types under the law, each with different roles and responsibilities. Businesses may fall into one or more of these categories depending on its activities. Most businesses will take advantage of one or more Service Providers.
- Identify your PI data flows – This step is necessary to find all of the PI within your organization, where it comes from, how it’s used, where it goes, and how it is disposed of. Don’t forget to verify that you have the consumer’s consent for all of this PI, and if you don’t, you need it!
- Identify all of your external entities and legal agreements – You will want to review all of your current contracts and agreements to ensure they contain language for CCPA compliance. Identify any gaps and work with your partners to close them.
- Perform a gap analysis of all CCPA requirements – Start with your internal policies and work outwards to your customer facing technology stack and public website.
- Remediation – Close gaps with process where you can and build a roadmap to deploy technology to automate self-service. Notify your consumers of all the changes you are making and prepare documentation for front-line support staff to answer questions.
- Plan for the future – Compliance is a constant practice, not a one-time project. Make a plan to monitor for changes in the law, review internal compliance with the new changes, review partner compliance, and develop improvements to increase compliance and improve customer experience.

The California Attorney General’s office will be publishing updates to CCPA on a regular basis as it ramps up to begin enforcement in July of 2020.
The update released on February 10, 2020, mostly added additional clarification to existing language, but also included a big new requirement: Web Content Accessibility Guidelines (WCAG) 2.1. All notices published online must be WCAG 2.1 compliant under CCPA.
As always, SecureTrust is standing by and ready to help. If you need help with CCPA, GDPR, or any other privacy regulatory scheme, please give us a call. We have expert consultants standing by all over the globe that can partner with you to help you understand the requirements, find the gaps, and plan for remediation.
____________
SecureTrust, a Sysnet company, leads the industry in innovation and processes for achieving and maintaining compliance and security. SecureTrust delivers world-class consulting, compliance and risk assessment services and solutions for the enterprise market as well as tailored merchant risk management programs and solutions for merchant program sponsors around the globe.
Contact us today for all Enterprise Compliance, Merchant Risk Management and Compliance Technology needs.
____________

Written by Jon Marler
Jon Marler is a Product Manager at SecureTrust with a true passion for information security and more than a decade of experience in information security, payment processing, risk management, software development, and telephony. Jon spent eight years working with some of the largest acquirers in the world, helping them build online payment gateways and risk management platforms before joining SecureTrust. Aside from his primary role with SecureTrust, Jon also sits on the EC-Council ANSI Scheme committee as a trusted advisor, has participated in the PCI SSC SIG focused on addressing cloud computing, and is a member of the ETA committee for mobile payments. As a result of his long-standing commitment to open source software, Jon has offered his expertise as a package manager for the Debian GNU/Linux OS distribution since 1998.
