This article applies to:
- External Vulnerability Scanning
Information:
Effective January 31, 2018, PCI External Vulnerability Scans may begin to fail “Host(s) Not Detected” finding caused by changes in the scan assessment requirements. Specifically, external vulnerability PCI scans may fail if some or all of the scan targets identified in your PCI ‘Scan Setup’ do not respond to our scanner in a timely manner. This means that you asked SecureTrust to scan a public target IP address that our scanner was ultimately unable to detect, and therefore unable to make a determination on the overall security of the environment. SecureTrust is a PCI Approved Scanning Vendor (ASV) and adheres to the latest ASV Program Guide (see this PDF).
How can I tell if I am impacted?
Review your scan results (or scan report) to see if there are any “Host(s) Not Detected” findings. For most PCI scan customers, look for a result like the screenshot below in your Scan Results screen:
For SecureTrust scan customers, your finding would look like this:
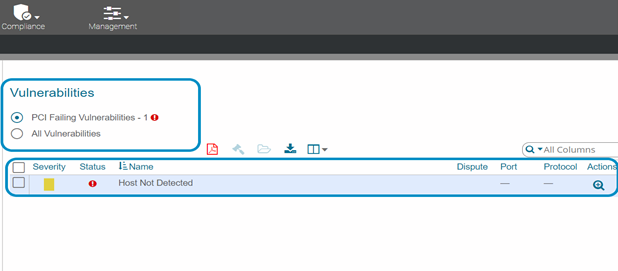
How do I correct these failures?
Targets in your Scan Setup that are flagged with this finding should be corrected and a new scan should be completed. In most cases, you may be able to simply remove the questionable host and initiate a rescan. Below are general steps for scan customers – review the steps that apply to your scanning product.
All scan customers should:
Check that your ‘Scan Setup’ has ALL of the current and correct IP Addresses and/or Domain Names listed as scan targets. To verify that the correct IPs are being scanned, follow the step-by-step instructions listed below for your scanning product.
Note that Dynamic IP addresses change frequently and may need to be updated prior to each scan.
Businesses using SecureTrust PCI Manager to update or remove scan targets.
Product icon:

1. Add correct scan location or verify that the IP/websites (domain names) are still accurate and applicable to you. Skip to step 5 if your Scan Setup is correct and current; you will just need to remove the Undetected Host target.
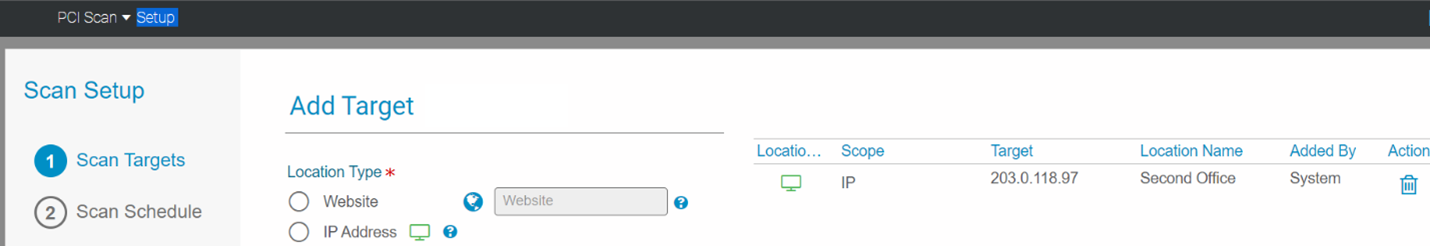
2. Add Website (domain) -OR- IP address (physical location):
3. Specify location type (website or IP address), scope, location name, disclaimer radio buttons, click Add: 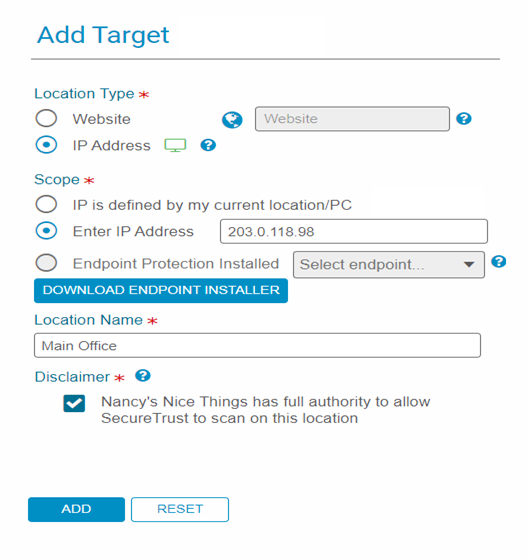
4. Attest to Scan Setup.
- You may be prompted with the attestation several times throughout the process.
- Utilize the Download Endpoint Installer shown below to improve the accuracy of targets being scanned by sending the scanner the correct location.
5. Remove erroneous location(s) – click the Trash Can icon:
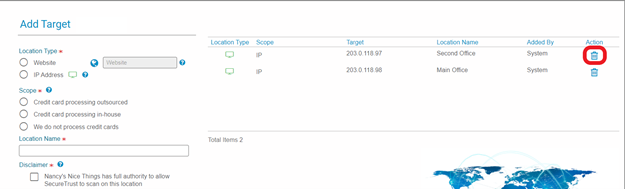
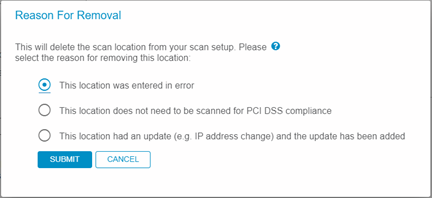
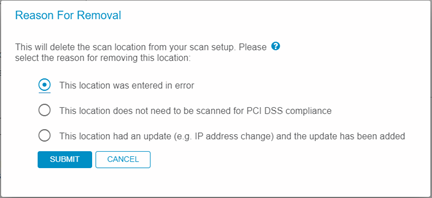
6. Specify reason for removal:
- Note: in most cases, the default reason (entered in error) should be selected to remove a target. However, please be advised that utilizing the second option will be recorded to section 4A of the next ASV report which runs from this profile. See the ‘ASV Program Guide 3.1’ for more details on section 4A of the ASV report.
7. Initiate a rescan.
Notes:
- All on-demand rescans are complimentary.
- The scan attestation may be presented several times throughout the process.
Enterprise or complex scan clients using SecureTrust Advanced Scanning to update or remove scan targets.
Product icon:

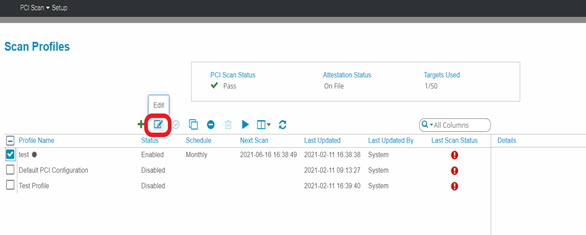
1. Analyze Scan Profiles listed in the table by ticking the check box on the left and choosing Edit to review the configuration.
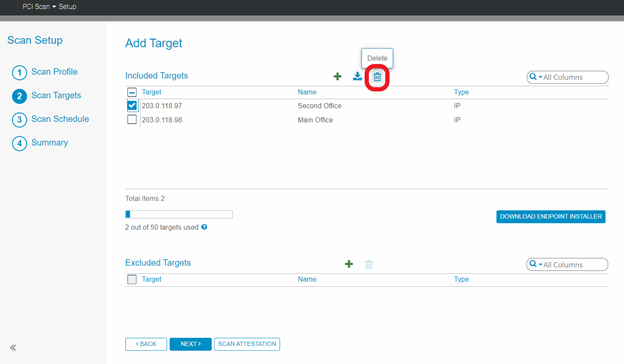
2. Analyze Included Targets. Work with your IT team/technical resource to determine if targets exist that are no longer part of your card holder data environment (CHDE). To remove the unneeded scan targets, select the targets and click the Trash Can icon.
3. Specify reason for removal:
- Note: in most cases, the default reason (entered in error) should be selected to remove a target. However, please be advised that utilizing the second option be recorded to section 4A of the next ASV report that runs from this profile. See the ‘ASV Program Guide 3.1’ for more details on section 4A of the ASV report.
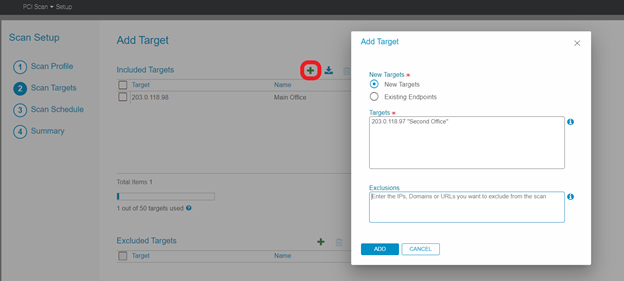
4. To add, click the green +. Enter Targets and Exclusions and click Add.
- The Endpoint Installer application can be downloaded to improve the accuracy of targets being scanned by sending the scanner the correct location done by the beacon feature.
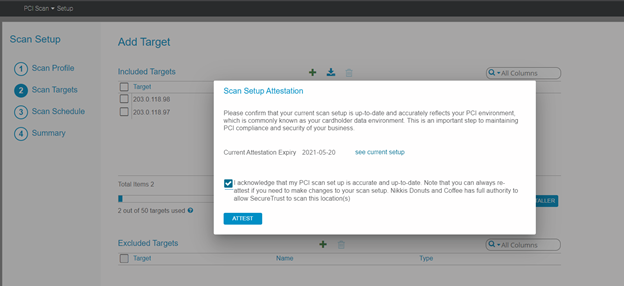
5. Attest to the new target, and review scan target list.
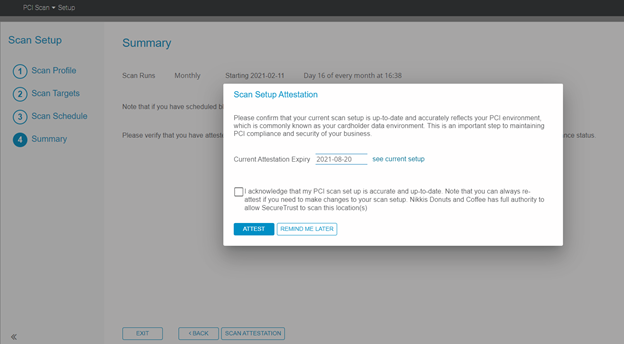
6. Review Steps 3 & 4: Scan Schedule and Summary to complete the scan setup. If the attestation window pops up, please Attest to continue.
- You may be prompted with the attestation several times throughout the process.
7. Clicking the Scan Now icon will initiate a scan to run immediately. Otherwise, the scan will continue to run on its regular schedule.
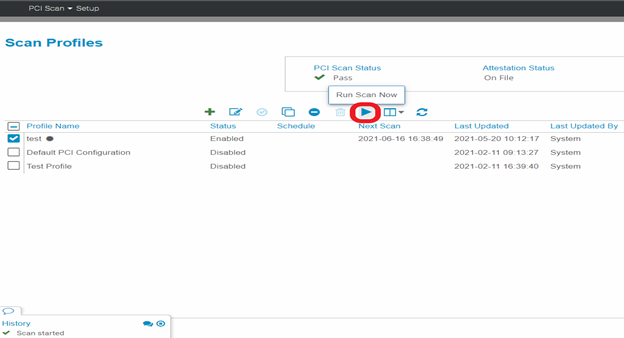
All scan customers – How do I correct these failures? (Continued from above)
1. Ensure SecureTrust’s PCI scanner is whitelisted on your Internet-facing security systems (like intrusion detection/prevention systems). Your IT/technical resources may be able to assist. (See Notes and Reminders section)
2. Check firewall settings to ensure that scan targets specified can be detected by the SecureTrust scanner.
- Important Note: PCI does not require your organization to reduce security levels in order for scan targets to be visible to the SecureTrust scanner.
3. If available, download and install the SecureTrust Endpoint Protection Suite software (EPS) on at least one system in the environment. Then ensure that your Scan Setup is using the SecureTrust Endpoint as its source. This software is designed to report the current IP of your device(s) back to SecureTrust, so we are always sure to be scanning the correct asset(s).
4. Using the above process, update your Scan Setup to remove the Host(s) Not Detected.
- Note: In-scope environments that are required for compliance but have outdated IP address or website can be removed from the scan setup. Be sure to add in the updated IP address or website domain name into your scan setup.
5. Initiate a rescan.
6. If a rescan continues to yield Host(s) Not Detected again, and you have already whitelisted SecureTrust’s scanner source IPs, then your network equipment may be hidden by design. A ‘hidden’ network is legitimate: the one important thing to make sure of is that the network must not be using ‘active protection systems’ (such as intrusion prevention systems) to block SecureTrust’s scanner (please see the ASV Program Guide v3.1, available on the PCI SSC’s website for more information).
- Note: In this situation you may raise a dispute via the SecureTrust Dispute process. The contents of the dispute must involve an attestation from the customer that both A) ‘the host is not visible because it is intentionally hidden (hidden by design)’, and B) ‘there are no active security measures present on the host being scanned’. A member of the SecureTrust Scan (ASV) team will review the dispute and work with your organization to rectify the situation.
7. During the dispute process, additional information regarding your organization’s network configuration may be required. Once the process is complete, and if the correct information is received, the dispute will be approved, and your scan report (unless pending other unaddressed vulnerabilities) will be automatically changed from FAIL to PASS.
Notes and Reminders:
- All on-demand rescans are complimentary.
- You may have received an email notifying you that your most recent scan has failed however you see all green checkmarks on your PCI dashboard. Action may be required if your most recent scan has failed, and updates will need to be made to ensure you remain secure and compliant year-round.
- Passing external PCI vulnerability scans are required on a quarterly basis (every 90 days). To support ongoing security monitoring, SecureTrust conducts these scans every month to ensure that you have appropriate time to make any necessary updates to your payment-processing environment before those 90 days are up.
- What is “Whitelisting”?
- In PCI scan context, ‘Whitelisting’ is a term that is equivalent to ‘granting access’. Some Internet devices (such as routers and firewalls) and security systems (such as intrusion detection/prevention systems) may have the ability to block unusual Internet activity. A PCI vulnerability scan may fall into the system’s category of “unusual activity”. Generally, the result of not whitelisting a PCI scan may be viewed as an obstructed scan or no scan has even occurred. Based on PCI ASV program rules, such scans must be deemed inconclusive.
- What are the SecureTrust scanner IPs?
- If you monitor your network for activity, note that the scan may originate from IP addresses in this range:
64.37.231.0/24 (64.37.231.1 through 64.37.231.254)
- If you monitor your network for activity, note that the scan may originate from IP addresses in this range:
- To learn more about the PCI changes, see the PCI ASV Program Guide v3.1.
- To contact SecureTrust about this article or to request support:
- Go to https://www.securetrust.com/support1/ OR
- Log in to SecureTrust Portal (https://portal.securetrust.com/).
